In today’s digital landscape, organizations face increasing pressure to demonstrate their commitment to data security and privacy. The SOC 2 Type 2 controls list has become a critical tool for companies looking to prove their robust security practices and gain customer trust. This comprehensive framework, developed by the American Institute of CPAs (AICPA), provides a structured approach to assessing and reporting on the effectiveness of an organization’s internal controls over time.
This article delves into the intricacies of SOC 2 Type 2 compliance, offering a detailed exploration of the controls framework and its key components. We’ll examine the essential security measures, data protection strategies, and privacy safeguards that make up a thorough SOC 2 Type 2 controls list. Additionally, we’ll discuss the benefits of compliance automation tools and provide insights on how to streamline the implementation process. By the end, readers will have a clear understanding of what it takes to achieve and maintain SOC 2 Type 2 compliance in today’s ever-evolving cybersecurity landscape.
SOC 2 Type 2 Framework Overview

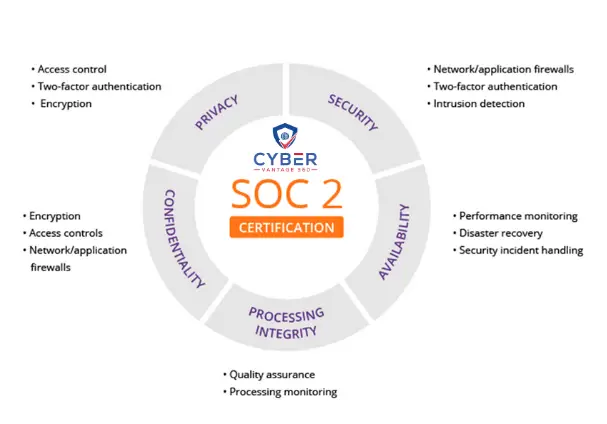
The SOC 2 Type 2 framework, developed by the American Institute of Certified Public Accountants (AICPA), provides a comprehensive approach to assessing and reporting on an organization’s internal controls over time. This framework is built upon five Trust Services Criteria (TSC), which form the foundation of an organization’s cybersecurity posture.
Trust Services Criteria
The five Trust Services Criteria are:
- Security: Protecting information and systems from unauthorized access, disclosure, and damage.
- Availability: Ensuring systems and information are accessible to meet the organization’s objectives.
- Processing Integrity: Verifying that systems operate as intended, delivering complete, valid, accurate, and timely processing.
- Confidentiality: Safeguarding confidential information by limiting its access, storage, and use.
- Privacy: Protecting personally identifiable information (PII) in accordance with the AICPA’s Generally Accepted Privacy Principles.
It’s important to note that while Security is mandatory for every SOC 2 audit, the other criteria are optional and can be included based on the organization’s specific needs and services.
Common Criteria vs. Additional Criteria
The SOC 2 framework distinguishes between Common Criteria and Additional Criteria:
- Common Criteria (Security): Also known as the Security Criteria, these are required for every SOC 2 audit. They encompass nine points of focus, including:
- Control Environment
- Communication and Information
- Risk Assessment
- Monitoring Activities
- Control Activities
- Logical and Physical Access Controls
- System Operations
- Change Management
- Risk Mitigation
- Additional Criteria: These are optional and include Availability, Confidentiality, Processing Integrity, and Privacy. Organizations may choose to include these based on business needs or customer requirements.
Audit Process and Timeline
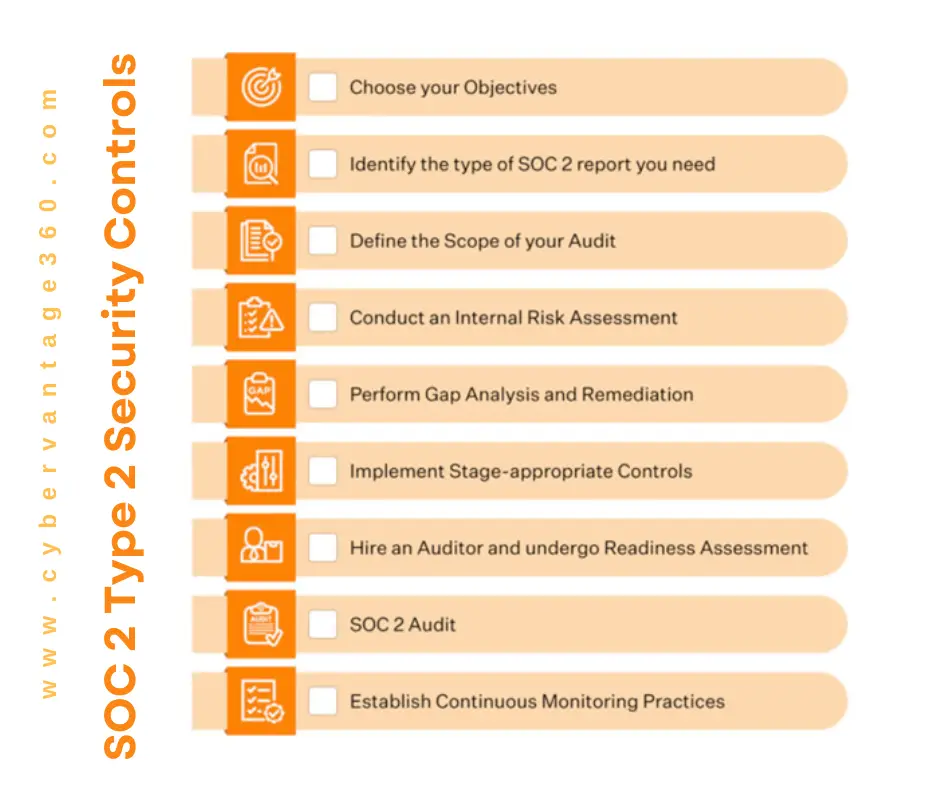
The SOC 2 Type 2 audit process typically follows these steps:
- Pre-Audit Phase (1-9 months):
- Select SOC 2 Type 2 audit
- Define audit scope
- Conduct gap analysis
- Complete technical configuration remediation
- Collect documentation
- Complete readiness assessment
- Audit Window Phase (3-12 months):
- Begin review period (typically 6-12 months)
- Collect evidence and document control performance
- Audit Phase (1-3 months):
- Start formal audit process
- Auditor performs control tests
- Gather evidence and interview team members
- Receive SOC 2 report
The entire process can take anywhere from 5 weeks to 15 months, depending on the organization’s readiness and the chosen audit window. It’s recommended to schedule SOC 2 audits every 12 months to maintain compliance and demonstrate ongoing commitment to security and privacy standards.
Security Controls
The SOC 2 Type 2 framework encompasses a comprehensive set of security controls designed to protect an organization’s information assets and ensure compliance with industry standards. These controls are crucial for maintaining the confidentiality, integrity, and availability of data while mitigating potential risks.
Access control forms the foundation of a robust security posture. It involves implementing logical and physical access security measures over protected information assets. Organizations must establish procedures for issuing credentials, authorizing access, modifying permissions, and restricting physical access to facilities and sensitive data.
Key components of access control include:
- Implementation of the least privilege principle
- Maintenance of an access control matrix
- Just-in-time provisioning for sensitive systems
- Regular user access reviews (UARs)
By adhering to these practices, organizations can significantly reduce the risk of unauthorized access and potential data breaches.
System Operations
System operations focus on detecting and monitoring procedures to identify changes that may introduce vulnerabilities. This includes:
- Implementing detection and monitoring procedures to identify configuration changes
- Executing a defined incident response program
- Monitoring system components for anomalies indicative of malicious acts, natural disasters, or errors
Organizations should utilize automated tools and processes to continuously monitor their systems and quickly respond to potential security incidents.
Change Management
Change management controls are essential for maintaining the integrity and security of an organization’s IT infrastructure. These controls encompass the authorization, design, development, testing, approval, and implementation of changes to infrastructure, data, software, and procedures.
Key aspects of change management include:
- Establishing a defined IT change management policy and procedure
- Utilizing change management tools, such as ticketing systems and code repositories
- Implementing separate environments for development, testing, staging, and production
- Conducting peer reviews and independent quality assurance testing
- Obtaining approval from a change advisory board (CAB) before deployment
By following these practices, organizations can ensure that changes are properly vetted and do not introduce new vulnerabilities into their systems.
Risk mitigation involves identifying, selecting, and developing activities to address potential business disruptions. Organizations should conduct regular risk assessments to evaluate the types of risks present as a result of their service commitments and system requirements.
Key steps in the risk mitigation process include:
- Identifying internal and external risk factors
- Assessing the likelihood and impact of identified risks
- Determining residual risk levels after considering existing controls
- Developing and implementing risk mitigation plans
By proactively addressing potential risks, organizations can better protect their assets and maintain compliance with SOC 2 requirements.
Incident Response
Incident response is a critical component of an organization’s security strategy. SOC 2 requires organizations to have a well-defined incident response plan that outlines the steps to be taken in the event of a security incident.
Key elements of an effective incident response plan include:
- Clearly defined roles and responsibilities for response teams
- Consideration of third-party involvement in incident response
- Annual testing of the incident response plan
- Continuous improvement through post-incident analysis and documentation
By implementing a comprehensive incident response plan, organizations can minimize the impact of security incidents and demonstrate their commitment to protecting sensitive data.
Data Protection and Privacy
Data Classification
Data classification forms the foundation of effective data protection and privacy strategies. It involves identifying, categorizing, and labeling data according to its sensitivity level. Organizations should implement a robust data classification policy that outlines objectives, taxonomy, and roles and responsibilities of data owners. This process helps in organizing data by importance, safeguarding high-sensitivity information, and streamlining data searches and retrieval.
There are typically three levels of data sensitivity:
- Low sensitivity: Public data with little to no impact if compromised
- Medium sensitivity: Internal or private data with some risk if compromised
- High sensitivity: Confidential or restricted data with catastrophic impact if compromised
Organizations can employ user-based, content-based, or context-based classification methods, or a combination of these approaches. Regular reviews of classification criteria and processes are essential to keep up with changing regulations and business objectives.
Encryption Measures
Encryption plays a crucial role in protecting sensitive data from unauthorized access. SOC 2 compliance addresses data encryption in section CC6 – Logical and Physical Access. Organizations should implement end-to-end encryption for all digital communications and encrypt data at rest on servers and other storage devices.
Key encryption considerations include:
- Implementing AES (Advanced Encryption Standard) encryption, preferably AES-256 for enhanced security
- Encrypting all data-bearing systems, including mobile devices and portable storage
- Ensuring cloud-hosted assets are encrypted both in transit and at rest
While encryption can impact system performance, especially on older systems, the benefits of data protection often outweigh the potential drawbacks.
Data Retention and Disposal
A well-defined data retention policy is crucial for managing data throughout its lifecycle. Organizations must establish guidelines for retaining different types of data, considering legal, regulatory, and contractual obligations. Key components of a data retention policy include:
- Identifying retention periods for various data types
- Defining procedures for secure data deletion when no longer needed
- Implementing processes to classify, retain, and delete confidential and personal information
While SOC 2 does not specify exact retention periods, organizations must demonstrate that they have processes in place to manage data retention effectively, particularly for confidential and personal information.
Third-Party Risk Management
As organizations increasingly rely on third-party vendors to manage sensitive data, effective third-party risk management becomes critical. SOC 2 compliance requires organizations to implement specific controls for managing vendor relationships and protecting data shared with external parties.
Key aspects of third-party risk management include:
- Conducting vendor risk assessments before onboarding
- Obtaining privacy and confidentiality commitments from vendors
- Regularly assessing vendor compliance with these commitments
- Implementing procedures for addressing issues identified during assessments
- Establishing protocols for terminating vendor relationships when necessary
Organizations should also ensure that vendors have proper incident response procedures in place, including notifying the organization of any actual or suspected unauthorized disclosures of personal information.
By implementing these data protection and privacy measures, organizations can significantly enhance their security posture, meet SOC 2 compliance requirements, and build trust with their customers and partners.
Compliance Automation and Tools
In the realm of SOC 2 compliance, organizations are increasingly turning to automated solutions to streamline their processes, enhance security measures, and maintain continuous compliance. These tools not only simplify the complex landscape of SOC 2 requirements but also provide real-time insights into an organization’s security posture.
Security Information and Event Management (SIEM)
SIEM solutions have evolved from simple log management tools to sophisticated platforms that offer comprehensive security monitoring and analysis. These systems aggregate log data from various sources within an organization’s computing infrastructure, providing valuable insights into security-related incidents and events.
Key features of modern SIEM solutions include:
- Real-time threat detection using advanced machine learning algorithms
- Flexible cloud-based deployment options
- Centralized logging capabilities
- Root cause analysis for potential security vulnerabilities
By implementing a SIEM solution, organizations can:
- Simplify compliance reporting processes
- Identify potential risks more quickly
- Maintain high standards of data integrity and system availability
- Enhance overall security posture
Governance, Risk, and Compliance (GRC) Platforms
GRC platforms offer a holistic approach to managing an organization’s compliance efforts. These tools help streamline various aspects of the SOC 2 compliance process, from risk assessment to continuous monitoring.
Key benefits of GRC platforms include:
- Centralized management of compliance activities
- Automated risk assessments and control monitoring
- Enhanced visibility into compliance status across the organization
- Streamlined reporting and documentation processes
Continuous Control Monitoring
Continuous control monitoring is a critical aspect of maintaining SOC 2 Type 2 compliance. This approach involves ongoing assessment of internal controls to ensure they are functioning as intended throughout the compliance period.
Key aspects of continuous control monitoring include:
- Risk-based approach to prioritize monitoring activities
- Regular assessment of key controls (at least annually)
- Variety of monitoring methods tailored to different control types
- Independence and competence of monitoring personnel
Automated tools play a crucial role in facilitating continuous control monitoring by:
- Flagging potential risks before they become compliance issues
- Providing real-time alerts for security incidents
- Enabling prompt corrective action when necessary
- Simplifying the audit process through detailed audit trails
By leveraging these compliance automation tools and implementing robust continuous monitoring practices, organizations can significantly enhance their ability to achieve and maintain SOC 2 compliance. These solutions not only streamline the compliance process but also contribute to a stronger overall security posture, ultimately building trust with clients and stakeholders.
Conclusion
To wrap up, SOC 2 Type 2 compliance plays a crucial role in building trust and demonstrating a company’s commitment to data security and privacy. The comprehensive framework, encompassing various controls from access management to risk mitigation, provides organizations with a structured approach to enhance their security posture. By implementing robust security measures, data protection strategies, and leveraging automation tools, businesses can streamline their compliance efforts and maintain a strong security stance over time.
Achieving and maintaining SOC 2 Type 2 compliance is an ongoing process that requires dedication and continuous improvement. Organizations that invest in this framework not only meet industry standards but also gain a competitive edge in today’s security-conscious business landscape. To get started on your SOC 2 compliance journey or to enhance your existing practices, reach out to us at info@cybervantage360.com for expert guidance and support.
FAQs
1. What exactly are SOC 2 Type 2 controls?
SOC 2 Type II reports focus on the Trust Service Criteria set by the American Institute of Certified Public Accountants (AICPA). These reports assess a service provider’s internal controls and systems in terms of security, availability, processing integrity, confidentiality, and privacy of data.
2. What is included in a SOC compliance checklist?
A SOC compliance checklist, also known as a SOC 2 audit or assessment checklist, includes guidelines, measures, and best practices that an organization should implement and adhere to in preparation for a SOC 2 audit.
3. What does SOC 2 compliance entail?
SOC 2 compliance is a voluntary standard for service organizations, established by the American Institute of CPAs (AICPA). It dictates how organizations should handle customer data based on criteria such as security, availability, processing integrity, confidentiality, and privacy.
4. How do SOC 2 Type 1 and SOC 2 Type 2 audits differ?
The main difference between SOC 2 Type 1 and SOC 2 Type 2 audits lies in their scope and timing. SOC 2 Type 1 evaluates if controls are properly designed at a specific point in time, whereas SOC 2 Type 2 assesses if controls are both properly designed and functioning effectively over a defined period.